The Cyber Security Operations Centre (CSOC) increases an organisation’s resilience to cyber threats. Aligned with the highest standards, it safeguards corporate data, IT infrastructure, and digital resources.



By leveraging the latest tools, such as SIEM, EDR and NDR, the CSOC team can maintain continuous surveillance over systems, networks and applications, identify suspicious activities, and quickly detect potential threats.
Network Detection and Response (NDR) provides the CSOC team with real time information about all activities within network traffic.
The Security Information & Event Management (SIEM) solution enables the collection, assessment and analysis of security events from all available sources (network devices, servers, applications, authentication systems, cloud services).

Warnings and incidents from different sources are thoroughly analysed to identify genuine real threats and assess their impacts.
Analysis begins with the collection of data from various sources. Correlation and filtering are used to isolate relevant incidents and to assess their severity. Detailed analysis supported by forensic tools is used to classify incidents according to risk levels and, if needed, to escalate the situation to the appropriate teams (e.g., IT, legal, management board).
For every analysed incident, a structured report is prepared outlining the findings and recommendations. Conclusions are used for continuous improvement of security controls, updating detection rules, and strengthening defensive strategies.
Using global sources of Threat Intelligence, the CSOC team can keep one step ahead of new attacks, vulnerabilities, and techniques.
Through deep analysis and continuous insight into the development of security threats, Cyber Threat Intelligence (CTI) recognises attacker techniques, active vulnerabilities, compromised access data, and threats specific to different industries. Information is collected from a variety of sources, including dark web forums, hacker repositories and data leaks, to public and private security bases.
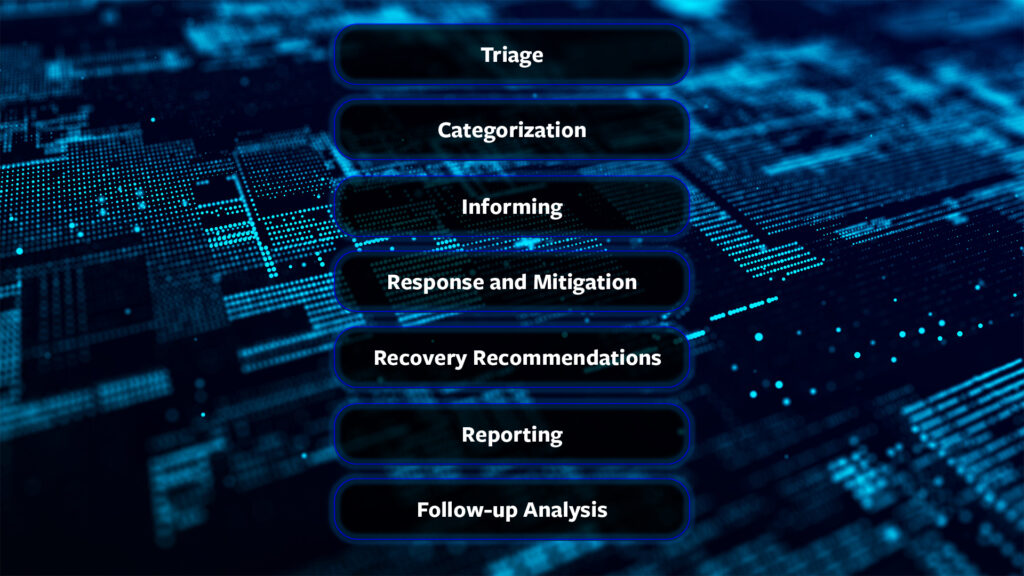
After a potential incident is detected, the CSOC team performs rapid triage to assess the urgency and severity of the incident. The incident is then categorised by priority (critical, high, medium, low) in order to ensure the optimal distribution of resources.
In order to prevent the incident from spreading, the CSOC team takes urgent measures (such as isolating a device or blocking an account). Additionally, the CSOC team informs the responsible teams and persons (i.e., IT, management board, DPO) in accordance with internal procedures and legal requirements (e.g., GDPR in cases of compromised personal data).
Final steps include restoring the system to a secure state, identifying the root cause of the incident and defining recommendations for recovery. The entire incident lifecycle is documented in the centralised system, including response times, actions taken, and conclusions. Detailed reports are compiled for the management board or regulatory bodies as required. After closure of the incident, the CSOC team conducts a post-incident analysis to learn from the incident, update security controls and procedures, and to raise awareness and vigilance.