From cyber threats to regulatory requirements – find out how you can strengthen your IT infrastructure and ensure digital resilience.
In today’s digital world, the question is no longer if we should implement digital transformation – it has become a necessity for survival in business and a key to competitiveness, no matter the activities of the company. Technological trends such as automation, artificial intelligence, cloud computing and edge computing change how data is managed, enabling better efficiency and adaptability to business challenges.
However, rapid digitalization is also imposing serious challenges – regulatory, technological and organizational. One of the most important ones is cybersecurity. According to the research of the American research company Gartner, more than 80% of companies in the world are already implementing digital transformation, which is accompanied by increased exposure to cyber threats. Attacks, such as ransomware, phishing, social engineering and AI generated threats are becoming increasingly sophisticated and frequent.
Get in touch for more information.
Anyone can become a target for attacks – critical infrastructure, supply chains, financial systems, business networks and individuals. For example, only during 2024, more than 1.3 billion people were affected by data theft and other cyber-attacks. The most frequent causes were security vulnerability in third-party software and insufficient preparation for cyber-attacks using AI tools.
Digital transformation brings huge opportunities, but also risks – and it is precisely cybersecurity that becomes crucial for protecting business operations in today’s dynamic environment.
Organizational and technological challenges of protection against cyber threats
Companies use different methods and tools to protect themselves against cyber threats, while at the same time they have to ensure compliance with regulatory requirements. In the European Union, of which we are part, companies are obligated to align their activities with rigorous legislation, such as the Digital Operational Resilience Act (DORA) and NIS2 Regulation.
DORA – new standards for digital resilience
The DORA regulation, in force since the beginning of 2024, sets new, stricter standards of operational behavior, in particular for financial institutions. This regulation sets a more comprehensive regulatory supervision system and demands frequent system stability tests. DORA also brings stronger consumer protection through thorough checks of software and other services providers.
It particularly emphasizes digital resilience as a key component of everyday business operations, especially for banks, insurance companies, organizations dealing with crypto assets and other relevant sectors.
NIS2 – Extension and strengthening of supervision
The NIS2 directive extends the scope of the previous NIS directive, including new sectors and shareholders, such as healthcare and public administration. This directive is also introducing stricter sanctions for non-compliance and improves the cooperation between EU member states. Whereas the previous NIS directive includes only key service operators and digital service providers, NIS2 also identifies key and important subjects, which extends the scope of the regulation.
Strategy for aligning with the regulations
To align itself with DORA and NIS2, each company has to develop a comprehensive digital resilience strategy. The first step in that process is risk assessment. Companies have to analyze in detail potential vulnerabilities in their IT systems, in particular those that depend on external software tools, infrastructure or service providers.
In addition, it is important to define clear rules of digital hygiene for all employees, including regular training sessions and checking compliance with regulations.
Technological solutions for resilience to threats
Companies need to implement technological solutions that guarantee data integrity. This includes regular copying of important information to multiple independent locations, as well as the use of threat detection systems based on artificial intelligence. It is also crucial to establish automatic response systems to cyber incidents that enable fast recovery from an attack and minimize downtime in business operations.
Continuous tests and employee education
In conclusion, all these measures need to be regularly tested through simulations and checks, whereas employees need to be constantly trained in data protection procedures and the use of tools for the protection against cyber threats.
This approach ensures that the organization is technically and regulatorily aligned, which is crucial for the maintenance of business stability and digital resilience in today’s threatening cybernetic environment.
Get in touch for more information.
Dell PowerProtect Cyber Recovery: Comprehensive data protection against ransomware threats
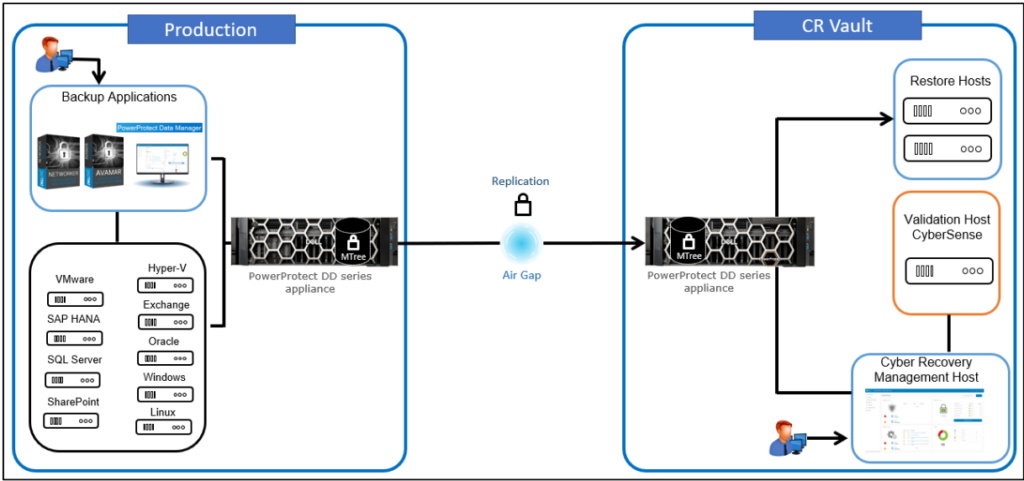
In this context, Dell PowerProtect Cyber Recovery solution offers a comprehensive response to challenges brought by ransomware attacks and other sophisticated threats. It enables organizations to protect their critical data and recover fast in case of an attack. Through advanced technologies, like isolated golden data copy, unmodifiable backup copies and secure data storage in air-gapped environment, Dell PowerProtect Cyber Recovery provides multilayer protection that minimizes the risk of data loss and enables the continuity of business operations.
Dell PowerProtect Cyber Recovery uses isolated golden data copy to create a safe, physically and logically separated storage for backup copies of data. In this manner, even if attackers manage to infiltrate the production environment, stored data remain protected from ransomware threats, enabling fast recovery.
One of the most important features of PowerProtect Cyber Recovery solution is non-modifiability of backup copies, that are stored in a format that prevents their modification or erasure. These backup copies are stored in WORM (Write Once, Read Many) format, meaning that attackers cannot manipulate them even if they do reach the system.
Dell PowerProtect Cyber Recovery includes analytical tools for discovering anomalies and data corruption, using CyberSense for file and database analysis. This tool can recognize unusual activities like files corruption, data encryption or unwanted modifications. When such activity is detected, it is possible to automatically substitute damaged files with the last known correct version of data.
Fast recovery and automated workflow
In case of a ransomware attack, Dell PowerProtect Cyber Recovery solution enables rapid recovery of data, thereby minimizing business downtime. Using automated recovery workflows, organizations can accelerate the recovery process and reduce financial and operational impact of an attack. Data recovery can last only a couple of hours, ensuring that business operations can continue unhindered.
Focus on regulatory compliance and data security
Dell PowerProtect Cyber Recovery not only protects data, but also helps organizations with their compliance with the newest regulatory requirements. The solution is fully aligned with DORA (Digital Operational Resilience Act) and NIS2 (Directive on security of network and information systems) that require organizations to implement data protection systems and regularly test their resilience to cyber threats. Dell PowerProtect Cyber Recovery enables companies to satisfy these regulations through strict supervision and testing resilience to cyber threats.
Conclusion: Refreshed resilience to cyber threats
Considering the velocity and seriousness of cyber threats, including ransomware attacks, companies have to invest in cyber resilience solutions that provide comprehensive data protection, such as Dell PowerProtect Cyber Recovery. Through isolation of backup copies, unmodifiable data copies and fast recovery, this tool enables organizations to recover fast in case of an attack, minimizing financial and operational damage.
Including analytical tools and automated recovery, Dell PowerProtect Cyber Recovery enables organizations to protect themselves against sophisticated threats and ensure long-term business continuity. With this solution, companies can safely manage their data, fulfill regulatory requirements and respond to threats with higher efficiency, ensuring tranquility and unhindered operation related to digital security.
Are you interested in Dell PowerProtect Cyber Recovery?
Contact us and we will advise you on the best solution for your specific needs. Allow our experts to strengthen your digital resilience and empower your cyber protection.